Courses I have taken in Berkeley
|
Term |
Course |
Grade |
Comments/Project
(s) |
|
Spring
1998 |
A |
Classic control course. |
|
|
ME128 Computer Aided Mechanical Design |
A |
Lots of programming! |
|
|
ME229 Design of Basic
Electro-Mechanical Devices (Prof. D. Lieu) |
A+ |
How motors are designed. |
|
|
Fall
1998 |
ME230 Real
Time Applications of Microcomputers (Prof. D.Auslander) |
A |
Computer control of physical systems
using C++ as implementation tool. Final project. |
|
ME232 Advanced Control Systems I (Prof.M.Tomizuka) |
A- |
Control theories. |
|
|
Spring
1999 |
ME233 Advanced Control Systems II (Prof.R.Horowitz) |
A |
Control theories. |
|
A |
Highly theoretical. Lots of Math! |
||
|
A- |
Expert system, fuzzy logic, etc. Project. |
||
|
Fall
1999 |
A+ |
The things behind the cool stuff on your
computer screen. See final project here! |
|
|
CS284 Computer Aided
Geometric Design and Modeling (Prof. B. Barsky) |
A |
B-Spline curves
and surfaces, NURBS... |
|
|
Spring
2000 |
EECS122 Communication
Networks (Prof.R.Sengupta) |
A+ |
Focus on Internet. |
|
ME235 Design of Embedded Systems
(Prof.A.Flynn) |
A+ |
Almost like CS150. Diverted to DSP after
midterm. Project. |
|
|
Fall
2000 |
CS152 Computer Architecture and
Engineering (Prof.
Bob Brodersen ) |
A |
The inner-workings of modern digital
computer systems and tradeoffs present at the hardware-software interface.
And how are they designed. Projects |
|
A |
A human centric view of computing and how
should future computing systems be designed. |
||
|
Spring
|
CS162 Operating Systems and
System Programming (Prof.
Anthony D. Joseph) |
A |
Design of operating systems and other
systems. Implemented Nachos. |
|
CS252 Graduate
Computer Architecture (Prof.
David A. Patterson) |
A |
More advanced stuff than CS152. Did a
project on Networked System Management. |
|
|
Fall
|
CS262A Advanced
Topics in Computer Systems (Prof.
Anthony Joseph and Joe Hellerstein) |
A |
|
|
CS186 Introduction to Database
Systems (Prof. Michael J.
Franklin) |
A |
The boring part of accounting
... |
|
|
Spring
|
Distributed
Service Architectures in Converged Networks (Prof. Randy Katz) |
A |
The convergence of traditional
voice-centric telecommunications networks, applications-focused distributed
middleware architectures, and the Internet. |
|
A |
Multiprocessors ... |
||
|
Fall
2002 |
A |
Protecting
User Data in Ubiquitous Computing: Towards Trustworthy Environments (PET
04) |
|
|
Spring
2003 |
CS270 Combinatorial Algorithms and Data
Structures (Prof. Christos Papadimitriou) |
A |
A
Secure Online Algorithm for Link Analysis on Weighted Graph ( |
|
Spring
2004 |
A |
How to
Construct Multicast Cryptosystems Provably Secure against Adaptive Chosen
Ciphertext Attack (CT-RSA '06) Scalable Secure Bidirectional Group
Communication. (INFOCOM '07) |
Selected Class Projects:
Three Axis Milling Machine (ME230)
Abstract
This projects hardware target is a three axis closed frame milling machine with a high-speed spindle. All of the components are off the shelf so that repair and maintenance is inexpensive and simple. The milling machine has a sturdy all aluminum frame. The aluminum frame is lightweight, and easy to manufacture using CNC machine tools. The revolutionary closed frame design increases rigidity and decreases the effect of thermal errors and Abbe' offset errors. Providing four posts for the Z-axis to ride on closes the frame. The working volume of this machine is 3"x3"x3".
The control software provides the best performance possible in the given time. The typical accuracy of the machine is 0.050 inches with speeds up to 15 inches per minute. The major features of the control software are:
Three Axis Milling Machine1. It is able to coordinate all three axes so that the cutter will move smoothly at a velocity (also called feed in machine tool industry) as constant as possible;
2. It has the capability to cut a part with arbitrary shape and certain complexity;
3. It has a user interface that takes inputs and displays enough information.The user interface anticipates the needs of the system’s users, and to make the necessary functions accessible and understandable. From this point of view, two kinds of use were accommodated. The first set of operations has to do with basic machine control of the sort an operator would be concerned with. The second was seen as addressing the needs of designers of parts or objects. The ability of designers to have a software path of access to the operation of fabrication equipment is the essence of intelligent, integrated manufacturing.
X38 Crew Recovery Vehicle Flight Controller Design Using D-K Iteration (ME234)
Abstract
The existing controller, Kx, does a good job on the nominal plant. But performance degrades at the presence of perturbation (9). The purpose of this project is to find a more robust controller, at the price of sacrificing performance on nominal plant. Worst case performance was analyzed.
More...
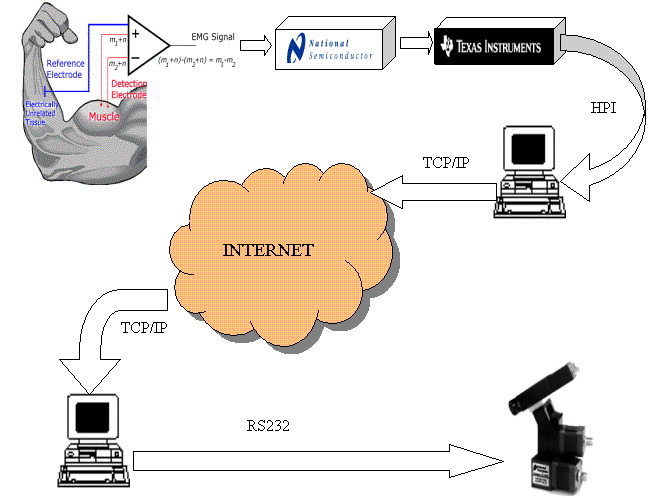
EMG Driven Internet Enabled Devices (ME235)
Abstract
We have undertaken a project to use the electrical activity that occurs in our muscles as an input signal for a device that will be controlled over Internet. This would allow for a more intuitive control of robots. It also allows handicapped people more freedom in interacting with their worlds. It was implemented using analog circuits, a Texas Instrument DSK board, two computers communicating via the Internet, and a servomotor from Directed Perception. The system currently functions very well and allows a camera to pan left and right as the user flexes different muscles.
DSP Enabled 5-Stage Pipeline Processor (CS152)
The goal of the final project is to implement a high performance microprocessor that executes DSP algorithms at minimum energy consumption. Basing the design on simple datapaths from the Patterson & Hennessey text, a 5 stage pipelined processor was created, operating at a cycle time of 29.8ns using SDRAM memory subsystem. Additional hardware was included in order to support DSP algorithms.
To support the Multiply and Accumulate (MAC) instruction for DSP, a MAC unit, which consists of a 2-stage pipelined multiplier, was added. The first multiplier was placed in MEM stage and the second one, together with a 32-bit adder, was fitted in the WB stage.
To speed up memory access time, the memory subsystem runs at double the clock rate of the processor. In addition, interface between memory compoenents are asynchronous whenever possible. Three separate controllers are used to control the instruction cache, data cache and its victim cache, and the sdram. An arbitrator is implemented as a simple asynchronous switch that coordinates between the controllers to determine access to the sdram without being responsible for data buses.
The instruction cache was chosen to have 20 words and is direct mapped because instructions are always sequential. The data cache, also direct mapped, has 28 words. A fully associative victim cache of 20 words is allocated for the data cache to improve performance. Since the cache block size is 4 words, the reading of the SDRAM also bursts 4 words. However, each write into the SDRAM consists of only 1 word using the write through policy with a 8 words write buffer.
Various methods were used to minimize power consumption. Input signals to components were balanced to arrive simultaneously. Power-hungry components were enabled only when required and disabled whenever possible. Pipeline stages were balanced by moving components to different stages to decrease the critical path. Unnecessary signals were removed and functions of components were reallocated. Balancing input signals proved to be the most efficient. For example, the energy consumed by the register file was successfully reduced from 400uJ to 216uJ, a 46% improvement.
Due to the added MAC support, critical path of our processor shifted from EX stage to MEM stage and the cycle time increased to 32ns (CLK-to-Q + 2nd stage multiplier + adder + 32-bit 2-to-1 mux). The current microprocessor uses 2.5volts of supply voltage and runs at 32ns cycle time. Running the dsp benchmark program under this specification yields an execution time of 600ms and consumes approximately 2.5mJ of energy. A large amount of this energy was used by the main controller, the hazard and forwarding units, the register file, and the memory subsystem. However, it is expected that the supply voltage will be reduced to 2.0volts while still meeting the project specifications.
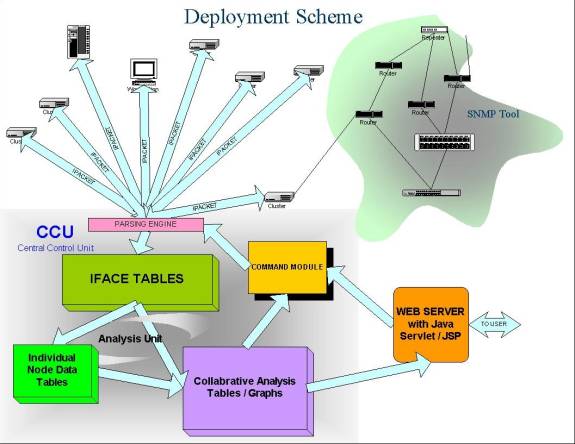
Networked System Management: Topology Discovery and Host Monitoring and Control (CS252)
Abstract
Computer systems are becoming more and more complex and managing them efficiently poses a challenge for system administrators. The increased complexity results from the following two trends in computer system development. 1) An individual computer, with the adoption of advanced (multi)processor, complex OS and fancy peripherals, is more sophisticated than ever. 2) Computers are getting more and more connected.
In this project we identified the needs in efficient management of networked, complex computer systems and proposed an approach to address them. We also implemented a basic set of tools to actually verify our approach. These tools were deployed and tested on Berkeley Millennium clusters [1].
Brocade: Landmark Routing on Overlay Networks (CS262A)
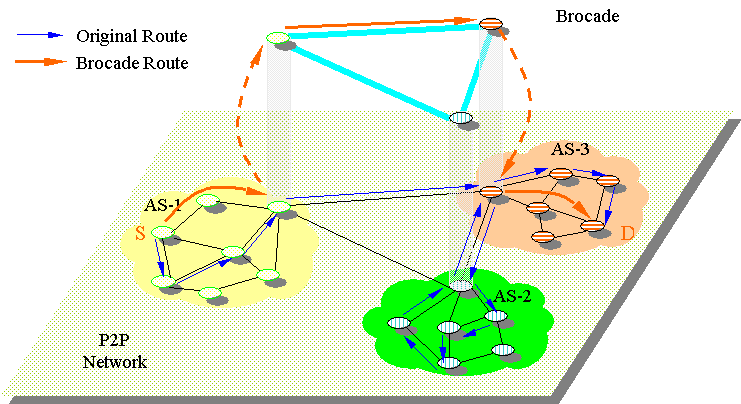
Abstract
Peer-to-peer networks offer attractive features such as decentralized computing, fault tolerance, sharing and aggregating of resources (e.g., SETI@home). A common (and limiting) assumption on peer-to-peer network is that, in order to achieve fair sharing and fault tolerance, all computers in the network should be considered equal and there should be no server nor explicit structuring in the network. Many theories and algorithms used by existing peer-to-peer infrastructures (such as Tapestry [12], Chord [9], Pastry [7] and CAN [4]) comply with this tenet. However, such systems often show sub-optimal performance due to the asymmetry of nodes in reality and the lack of structure among them.
In this paper, we argue that a peer-to-peer system does not have to operate in a pure peer-to-peer fashion to obtain the advantages mentioned above. We believe that such system can benefit from some form of internal organization and differentiation among its nodes, thus enjoying the efficiency of a well-organized system, while still providing users with the P2P features.
As a proof of our belief, we proposed and simulated Brocade, a secondary overlay to be layered on top of these systems. Brocade exploits knowledge of underlying network characteristics and recognizes the differences among the nodes. Simulations were run on the GT-ITM [11] transit stub topology and showed encouraging results.
Fuzzy Rule Based Experts System for Human
Thermoregulation Model (ME290M)
|
Abstract This paper investigated the application of fuzzy rule
based expert system (FRBES) to the identification of human thermoregulation
system which has long been modeled as a crisp controller without adaptation
by earlier approaches. In this project, human body is treated as an adaptive
fuzzy logic system. An additional fuzzy controller is implemented and its
effect studied. A fuzzy IF-THEN rule base consisting of a set of intuitive
fuzzy rules is constructed and applied to the fuzzy thermal controller. |
|
Hierarchical Modeling,
Manipulation and Animation of Human Body (CS184)
|
Abstract In this project we built a hierarchical model of a human
body out of a set of unorganized polygons. Necessary information was inferred
from the original data to define the relationship among body parts and enable
user manipulation. Special efforts were made to ensure correct modeling and
rendering of joints. Animation was achieved by recording a
sequence of frames and replay them. Although this is basically a
modeling project, we did our best to refine the rendering. We implemented a
surface normal calculation algorithm proposed by H. Hoppe[2]
and precalculated surface normal. Using this
information, we did a smooth shading rendering. |
|
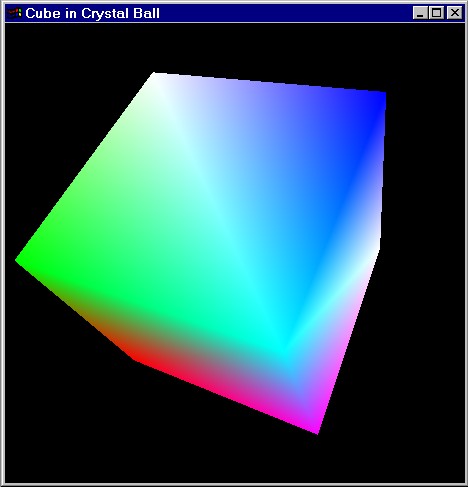
Cube
in Crystal Ball (CS184)
|
|
Implemented a crystal ball interface. The
cube can be manipulated by mouse. Moving the mouse with left button pressed will
rotate the cube about an axis through its center and perpendicular to the
viewing plane. Dragging the mouse with middle button pressed rotates the cube
about the vertical axis in the viewing plane. The angle rotated is
proportional to the distance the cursor travels. This project is mainly about the concepts of 3-D
transformation and perspective projection. No OpenGL 3-D transformation
functions, e.g. gluPerspective, glRotate,
etc., are called. Nor are the OpenGL matrix functions, glPushMatrix,
glMultMatrix, etc., used. Instead, I developed a
simplified version of "GL libriary" which
enabled me to do basically the same things. The color effect was achieved by assigning different
colors to each vertex, instead of each surface, and using smooth shading. |
3D
Maze (CS184)
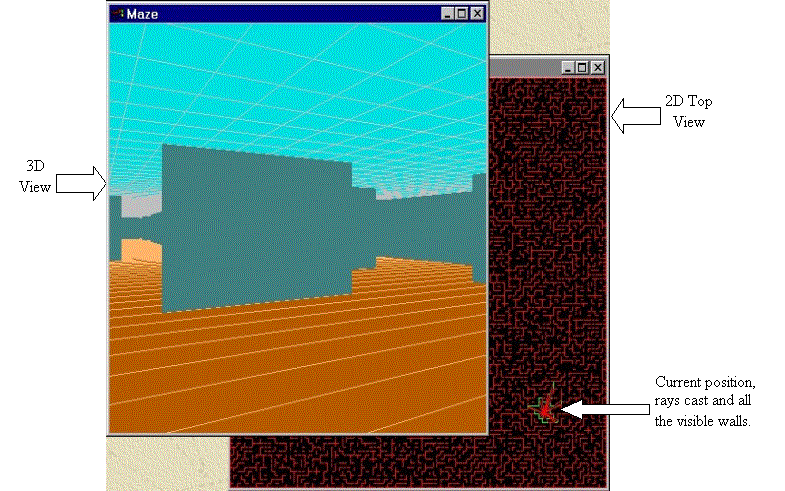
Basically this is a visibility problem. To render, in 3-D, a maze with a large
number of cells(100x100), the conventional Z-buffer
method won't work effectively. The huge amount of unnecessary rendering of
pixels will slow down the speed to a screwl.Instead, we calculate the visibility of cells and only render those
that are visible while the user is at certain position and viewing at certain
direction.
Shells
(CS184)

Evaluating
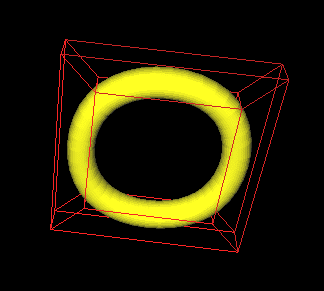
a NUB Surface(CS284)
|
A torus formed by tensor
product cubic b-spline patch with its control mesh |
Implemented an algorithm evaluating
Non-Uniform B-spline (NUB) surfaces using knot
insertion. The knot insertion algorithm used is a modified version of Boehm
algorithm which is basically the first level of de Boor recursion. This
algorithm allows to insert knot at any parameter
value within any knot interval within the legal parameter range. The original
algorithm, however, does not eliminate the first and the last control points.
As a result, part of the control polygon will converge to the curve and there
will be some extra pieces left. The following was done to solve this problem:
Insert knots in the legal parameter range AND one
interval before and after it. Use a phantom control vertex at the beginning
and end respectively, which are just the copies of its neighbors. Also extend
the knots one unit to the left and right. Now we have a well-defined set of
control vertices and knot sequence to insert knots in the intervals right
before and after the legal parameter range.Do the knot insertion. Eliminate the extra
control vertices resulted from phantom control vertices and extended knots.
Also throw away the extended knots. What left is a
refined knot sequence and a set of control vertices which is closer to the
curve. |
[Home] [Courses] [Research] [Resume]
Last updated