Briefly sketch answers to each of the following problems. Two or three short sentences should be enough for nearly all of the questions. Feel free to use incomplete sentences if you like.
This problem set is due Tuesday, 24 September. Turn in your answers, in paper, at the beginning of class that Tuesday.
You may discuss the questions on this homework with others, but the writeup you turn in must be your own. You may use any source you like (including other papers or textbooks), but if you use any source not discussed in class, you must cite it.
Which of the vulnerabilities described below would likely have been avoided if the system had implemented in Lampson's message-passing model?
Malicious Max has planted a malicious Trojan horse in your favorite web browser, unbeknownest to you. This is unfortunate, because you frequently use your web browser to access your bank account online, and Max would like nothing better than to steal your bank balance. Max has already set up the backdoor to silently capture your account number and password; now he needs to find a way to get this information off your computer and across the network back to himself.
List at least three covert channels that Malicious Max could use to leak information about your banking secrets to a colluder at large somewhere in the network. Can you find one that cannot be easily detected by a knowledgeable defender who can passively sniff on all network traffic?
You're the dev lead on a networked multiplayer game, and it's still early in the design process. Two different architectures have been proposed (see below). Which one is likely to have better security properties?
In the first proposal, the software is split up into three components: a network shim (a very small piece of code that opens a socket and translates between network packets and internal data formats), a game engine (a large chunk of code that manages game strategy and evolution), and a renderer (a large chunk of code that prepares gorgeous graphics).
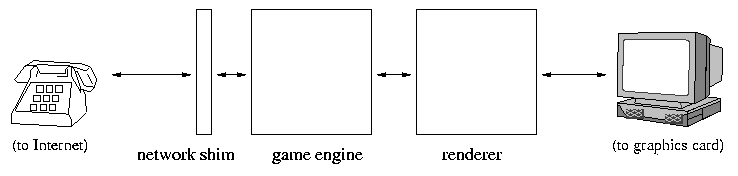
In the second proposal, the software is split up differently: there's a game core (like the game engine, but it talks directly to the Internet rather than going through the network shim), a rendering engine (most of the code of the renderer, which figures out what to draw), and a graphics card shim (a very small piece of code which translates the rendering engine's output into a format understood by the graphics card).

In the above, large boxes represent hundreds of thousands of lines of code; small boxes represent thousands of lines of code; and lines represent connections between components. Because the game listens on a low-numbered port, opening a socket will require special privilege, and so the piece of code that talks to the network (network shim or game core) runs with root/Administrator privileges; the remainder runs under the user's account.
HTML can be viewed as a crude programming language, with security-relevant features like references to resources (e.g., A HREF links). How well does HTML follow capability discipline?
(Hint: If you're stuck, you could think about the scenario where the user is sitting behind a firewall and viewing HTML content generated by an untrusted server on the outside. Also, keep in mind that following a URL is an action that might have a side-effect: consider, e.g., web interfaces to databases.)