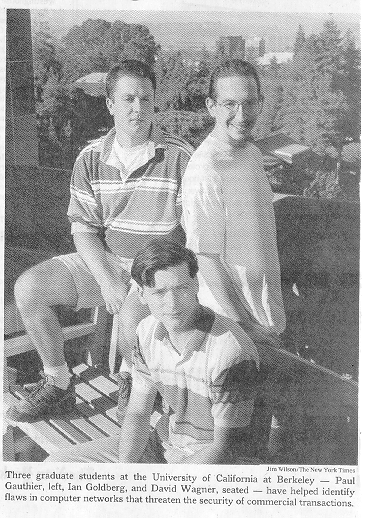
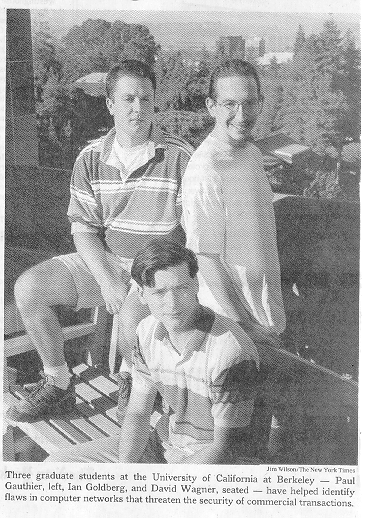
SAN FRANCISCO, Oct. 15 - Think of them as a truth squad of cyberspace.
Last Monday, for the second time in three weeks, crusading graduate-student hackers from the University of California at Berkeley publicized a flaw in computer network technology that they say threatens the security of commercial transactions over the global Internet. Just as they had done with a separate security lapse they identified late in September, the Berkeley computer scientists posted their findings on the Internet's World Wide Web and on several, on-line discussion groups.
As self-appointed fault finders, the students, with the full backing of a Berkeley computer science professor, are following the hacker subculture's time-honored tradition of ferreting out and publicizing imperfections in the endless quest for software perfection.
And yet, in a wrinkle hinting at a philosophical shift in the computer crusader tradition, the Berkeley hackers do not seem driven by the anti-establishment, freedom-of-information radicalism that has often colored such efforts.
Representing a new generation that seems more vigilant than vigilante, the Berkeley crusaders may typify a new willingness to accommodate Big Business on the Internet - as long as Big Business isn't trying to dupe the public with technology that is not as safe or secure as advertised.
"If they make strong claims about security, especially if they're not true, then they can't yell foul when someone discovers their flaws," said Ian Goldberg, a 22-year-old computer science graduate student who has been involved in the two recent disclosures.
Toiling in a windowless room jammed with computer work stations on the Berkeley campus, Mr. Goldberg and several colleagues, with the help of Prof. Eric Brewer, have put the business world on notice: With businesses rushing to put every conceivable kind of commerce on the Internet, companies that make claims of total security for financial transactions are going to find those claims quickly tested.
Several weeks ago Mr. Goldberg, along with another student, David Wagner, discovered a troubling flaw in the security of a Netseape Communications Corporation software program designed to let people safely make credit card purchases via the World Wide Web. Netscape acknowledged the weakness and quickly put out a corrected version of its program.
Last week Mr. Goldberg and Mr. Wagner, along with their fellow student, Paul Gauthier, and Professor Brewer, publicized several other security shortcomings in network software commonly used on computer systems connected to the Internet. The problems, they said, could enable a dedicated criminal to disable the security on even the new version of the Netscape software, or to make other mischief that might have nothing to do with Netscape's product.
These newly publicized flaws were generally known among software engineers who have developed and maintained the Internet since its creation more than 25 years ago. But the Berkeley hackers are bringing these underlying weaknesses to the public's attention to suggest that building truly robust security into the Internet - a network originally set up as an academic research experiment - may take more time and effort than some companies said.
Mr. Goldberg and his partners are followings tradition that emerged almost from the beginning of the computer industry in the years after World War II. The breed of computer software savants who would come to be known as hackers were preoccupied with analyzing complex hardware and software systems of all kinds to find their weak points - whether as an exercise in intellectual one-upmanship or in hopes of eliminating the flaws to create a perfect system.
Although intruders and break-in artists over the years have adopted some of the same methods with sinister intent, the true hackers were - and continue to be - motivated by a quest for technological truth.
"This is a tradition of unfettered inquiry and curiosity," said John Gilmore, a member of the board of the Electronic Frontier Foundation, a cyberspace public policy group. "For hackers, nothing is sacred and everything is subject to verification before you can really believe it."
This tradition has often grated against more conservative business cultures that wanted to keep information about computer security a closely guarded secret. Even now, the nation's official watchdog agency for computer security, the Government-financed Computer Emergency Response Team, based in Pittsburgh, tends to be fairly tight-lipped about security flaws that it discovers or that are brought to its attention. It will not publish the names of the organizations that have been attacked by computer intruders and usually only publishes limited details about the nature of newly identified software security flaws.
"It's always a tough call," said Tom Longstaff, the team's manager of research and development. "We've become a little more liberal recently, but it would be irresponsible to publish information permitting people to break into computers across the Internet."
Far different is a strain of vigilantism that has run among hackers for decades, and was typified earlier this year in a guerrilla tactic by Dan Farmer, a network security specialist. Mr. Farmer created and distributed over the Internet a program called Satan, which can probe for chinks in the armor of any computer system connected to the global network.
Mr. Farmer said he was unleashing Satan as a service to conscientious systems administrators at corporations, universities and government agencies so they could use the software to find and fix weak spots in their network defenses - and as a prod to apathetic or indolent administrators to force them to batten down the hatches.
But his action was considered so provocative and engendered so much controversy that his employer, the work station maker Silicon Graphics, dismissed Mr. Farmer, even though he had designed and distributed Satan on his own time with his own resources. (Silicon Graphics' rival, Sun Microsystems, recognized hacker talent when they saw it and quickly hired Mr. Farmer.)
Though only a few years younger than Mr. Farmer, Mr. Goldberg, the Berkeley student, seems to embody a new, less confrontational approach. It is an attitude that some experts see emerging among hackers who are coming of age at a time when the traditionally nonprofit Internet is turning into a commercial medium - like it or not.
Mr. Goldberg gives high marks to the way Netscape has handled itself in the face of the public scrutiny he helped engender. Last week, after introducing a new version of its software without the flaw that Mr. Goldberg and his colleagues identified in September, the company announced a contest called Netscape Bugs Bounty, which offers rewards up to $1,000 to people who discover and identify security loopholes in its products.
Paying money for something that true hackers have always considered a higher calling might have been derided as crass commercialism by earlier Internet enthusiasts. But not in these gold rush times.
"Most of what they've done so far is reactionary, but Netscape is to be commended," Mr. Goldberg said.
The implicit collaboration between hackers like Mr. Goldberg and companies like Netscape suggests that the computer culture that spawned the hacker ethic - the philosophy that information should be freely shared among computer users - may be resigning itself to, if not completely accommodating, the stampede to commercialize the Internet.
"The hacker ethic is transferring some of its better lessons to the world of commerce," said Steven Levy, author of the sociocultural book "Hackers."
"We're groping for a way to use the Net in a way where information will flow freely and people can still make money," Mr. Levy said. "The hackers are going to help us find ways to have a more humanized system of commerce."
But any companies lulled into thinking that the new era of accommodation means less vigilance, should have been in that windowless room in Berkeley last Friday.
"Today our computers were down, and so we just sat around and talked for a change," Professor Brewer said. "In less than a hour, we were able to think of 10 other attacks that many of these systems are probably vulnerable to."