1. Motivation
Requirements that arise frequently in communication systems include:
-
Confidentiality - only the intended recipient(s) can access the information,
-
Integrity - the data has not been modified,
-
Authenticity - the sender is the stated party.
The goals of cryptography are satisfying these and related requirements.
2. Encryption
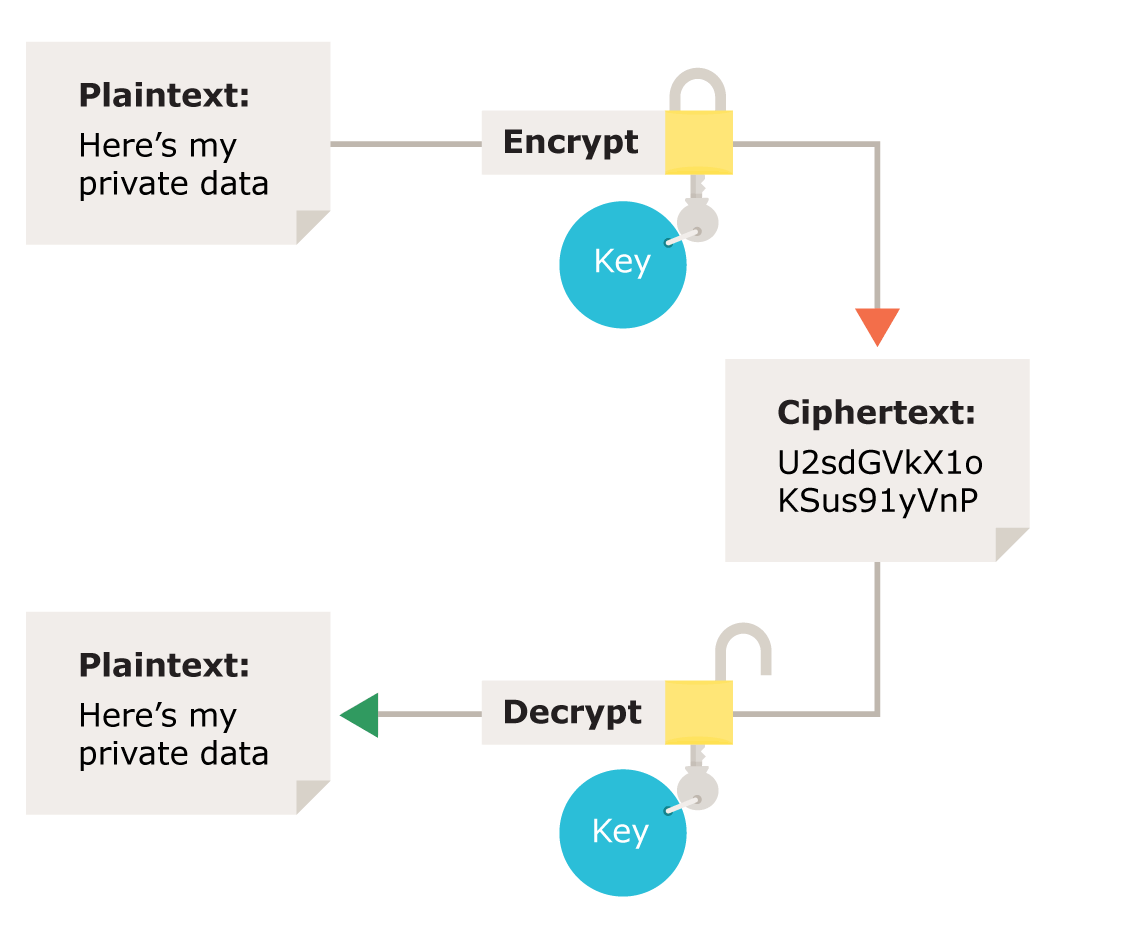
Encryption is a process of encoding a message or information in such a way that only authorized parties can access it and those who are not authorized cannot. As illustrated in Figure 1, the information or message, referred to as plaintext, is encrypted using an encryption algorithm – a cipher – generating ciphertext that can be read only if decrypted.
Usually, encryption schemes use a pseudo-random encryption key generated by an algorithm. It is in principle possible to decrypt the message without possessing the key, but, for a well-designed encryption scheme, considerable computational resources (which may not exist at the current time) and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users.
Two types of encryption are used in practice: symmetric key encryption requires that the sender and recipient are both in possession of a secret key and therefore requires some means to securely exchange keys. Public key encryption removes this constraint.
Since public key encryption is more computationally demanding than symmetric key encryption, many implementations use public key encryption to transmit the secret key. Subsequently more efficient symmetric key encryption is used.
2.1. Symmetric Encryption
A straightforward approach to ensure the confidentiality of a message is to place it in a locked box and distribute keys only to the intended sender and receiver(s). Electronic communication systems replace the physical box and keys with digital algorithms that transform a message into an unintelligible sequence of bits from which the original message can be recovered only with the key, which is also a sequence of bits (Figure 2).
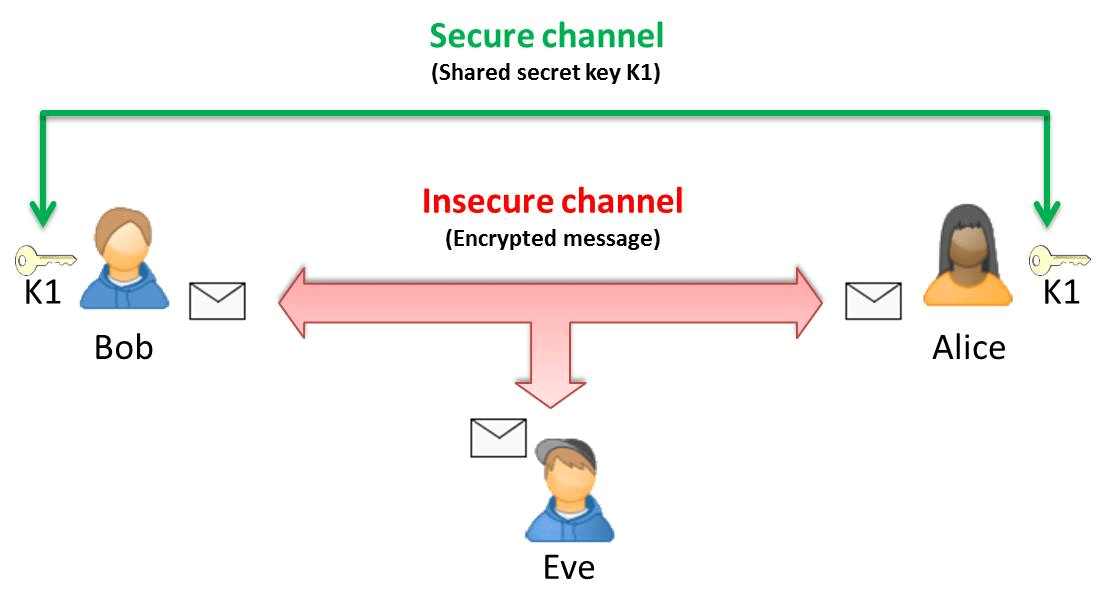
The requirement to distribute “secret” keys to only the intended recipients often poses problems. For example, if, as is often the case, the Internet[1] is the only means of communication, mailing the keys risks them being intercepted by a third party.
2.2. Public Keys
Public Key Cryptography eliminates the need to distribute confidential keys and thus eliminates the requirement for a secure, secret channel.
Instead of a single key, public key cryptography uses a pair of keys, one private and the other one public (Figure 3). The keys are large binary numbers, typically several hundred bits each that are near impossible to guess, even with contextual information such as the other key or encrypted messages.
The private key is kept secret. Since it is used only by one party and therefore does not require distribution, this requirement is easier (though not easy) to meet than keeping keys secret that are shared among several parties.
No requirement for confidentiality is placed on the public key.
The public and private key have the property that a message encoded with one can be recovered only with the other. As illustrated in Figure 4, if a message is encrypted (“locked”) with the public key, the original data can be recovered only with the private key. Likewise, a message encrypted with the private key is recoverable only with the corresponding private key.
“Only” in this context means that breaking the encryption using known algorithms requires a level of computational resources that is not available to a potential attacker. Obviously, given increasing compute power, this is somewhat of a moving target. In practice the strength of keys (generally the number of bits) is chosen such that they remain secure for at least as long as the information must be kept confidential, typically many years.
Public key encryption has many applications. The most obvious is ensuring confidentiality and data integrity. Other uses include ensuring the authenticity of the sender, non-repudiation, crypto currencies, etc.
3. In what situations should cryptography be used?
Using cryptography to secure communications channels incurs quite a bit of overhead in implementation, deployment, and continued use of computational resources. Naturally the question arises if the effort is really necessary for example to just communicate a few sensor values.
While unsecured systems operating in protected environments for testing may be defensible, accepted practices for securing system should be applied in virtually all cases. The purpose and usage scenarios change, often beyond the imagination of the inventors, and what may not have required full attention to security suddenly does.
Moreover, apparently benign unsecured microcontrollers can be weaponized by a determined attacker with potentially deadly consequences when e.g. life sustaining equipment in hospitals is affected. Deciding if an application requires encryption is easily substantially more difficult than simply following established practices.
Phil Zimmermann, one of the pioneers in widespread use of encryption, argues that consequent use reduces the risk of encrypted messages from standing out, thereby possibly raising the attention of a possible attacker.
Finally, including security in the initial planning of an application is simpler than later retooling.
There are few reasons not to secure an IoT application.